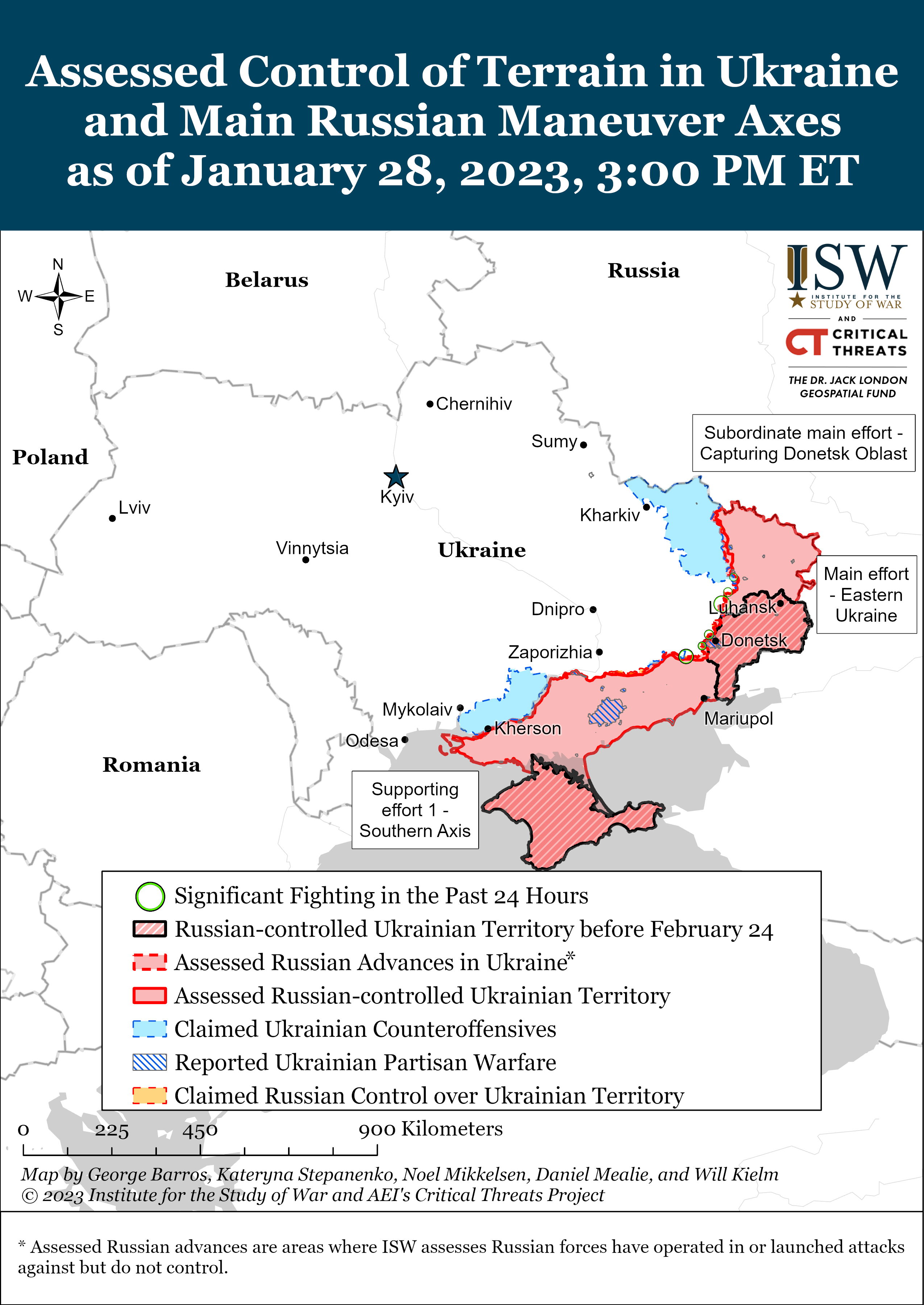
Because the warfare in Ukraine nears its eleventh consecutive month, the current excessive casualty strike carried out on New 12 months’s Day by the Armed Forces of Ukraine (AFU) in opposition to a Russian base in Makiivka has highlighted the significance of Operational Safety (OpSec). Following this assault each official and unofficial sources together with the Russian Ministry of Protection (MOD) claimed that Russian items had been recognized and focused as a consequence of their use of unencrypted cellphones. Ought to this be confirmed true, it will not be the primary time that the AFU have exploited the shortage of OpSec inside the Russian army and highlights an more and more endemic risk to the Russian operations.
Using mobile phone alerts to establish enemy positions is certainly not a brand new tactic in trendy conflicts. Each the US and UK army employed cell phone monitoring software program put in aboard modified King Air 350ER particular mission plane to find and establish excessive worth targets throughout counter-terrorism operations in opposition to Al-Qaeda and ISIS. Western strategists and their worldwide counterparts have repeatedly highlighted the dangers posed by servicemembers’ private cell gadgets, with quite a few NATO forces having applied stringent OpSec procedures throughout operational deployments to mitigate this risk. Russian army strategists are additionally conscious about this threat, having employed EW to good impact throughout the ‘chilly’ levels of the warfare between 2014-2022 and to some extent throughout the ongoing invasion of Ukraine to trace AFU troop actions. The Russian army has additionally skilled a number of OpSec failures lately throughout operations in Syria and through home workout routines, with social media posts by Russian troopers having been used to geolocate troops, establish delicate gear and even carry legal accusations in opposition to the Russian state, as was illustrated by the inquiry into the taking pictures down of economic airliner MH17. But regardless of the Russian army’s familiarity with this risk, there have been a number of high-profile cases of Russian forces together with excessive rating officers being recognized, focused and eradicated as a consequence of their frequent use of unsecured mobile communications, leaving observers to query, why Russian army forces have remained unable to mitigate this strategic risk?
The first purpose for this failure revolves across the inherent inadequacies of Russian army hierarchy and management with regards to forming a unified and disciplined combating power. Studies during the last a number of years have highlighted the endemic corruption and nepotism which have plagued Russian army command, with insufficient coaching and poor management been additional exacerbated by the absence of a devoted cadre of non-commissioned officers (NCO) all through the companies. This has resulted in a widespread lack of tactical self-discipline amongst Russian servicemembers, with using unsecured cellphones and the dissemination of delicate data proliferating as a direct consequence of those failures. Since Russian forces first annexed Crimea and infiltrated the Donbass in 2014, civilian analysts from outstanding establishments reminiscent of RUSI and Bellingcat have relied on open-source intelligence (OSINT) to confirm the presence of Russian army items in Ukraine utilizing photos and social media posts revealed by Russian troopers. The Russian MOD responded to this concern by confiscating the cellphones of Russian forces previous to their deployment to the Ukrainian theatre in February 2022. Nevertheless, the Russian excessive command’s failure to speak vital intelligence to frontline items led to an extra breakdown in self-discipline, with numerous documented cases of Russian forces confiscating cellphones from Ukrainian civilians, typically with deadly power, to accumulate communications capabilities and regain a point of situational consciousness.
The results of this insufficient hierarchical construction and management are much more pronounced amongst the Russian proxy forces, with the much less disciplined militias of the Donetsk Individuals’s Republic (DPR) or the Luhansk Individuals’s Republic (LNR), seemingly incapable of sustaining OpSec all through the battle. This resulted in a number of vital strikes in opposition to massive concentrations of DPR and LNR forces in the summertime of 2022, whereas the primary operations base of the Russian Wagner personal army company in Popasna was destroyed by a strike in August 2022 after photos posted on-line allowed the AFU to pinpoint its location. That strike was notable because it didn’t contain any interception of communications by the AFU’s EW items, however reasonably a easy but expensive failure in OpSec by Russian forces. This disparity in professionalism and experience has solely been additional compounded in current months by the Russian army’s conscription drive and Wagner’s recruitment efforts from jail populations, each of that are leading to poorly disciplined fighters being deployed en-masse to the Ukrainian frontline in a determined effort to offset mounting Russian casualties.
Along with the failure of Russian army management and self-discipline, the shortage of a viable encrypted communications answer has meant that even probably the most disciplined components of the Russian armed forces are in lots of instances obligated to make use of cellphones and different unsecured gadgets all through the battle. The Russian army does possess a army cryptophone system referred to as ‘ERA’, which might theoretically enable Russian forces to speak securely in theatre utilizing specialised encrypted radios and terminals. Nevertheless, the ERA system was designed to depend on current communications and mobile networking infrastructure, which was closely disabled by Russian strikes within the early days of the warfare. After Russia focused quite a few 3G/4G LTE antennas and masts in a bid to undermine Ukrainian communication capabilities, the shortage of mobile broadband protection additionally left their very own forces unable to speak securely. This strategic mistake proved extraordinarily expensive throughout the opening months of the battle, with US officers having confirmed in March 2022 that top rating Russian army officers had been focused and killed by precision artillery strikes after the AFU (and probably its US ally) had recognized their actual positions utilizing EW capabilities to intercept unencrypted radio and cell phone communications.
The instant influence of this error was additional exacerbated by the extra failures of Russian army logistics. Although Russian forces had been conscious of the risk posed by the shortage of encrypted communications, the endemic corruption inside the Russian army coupled with the sanctions imposed on the home protection business prevented the Russian MOD from supplying their forces with sufficiently superior options. There’s proof that in March 2022, Russian items had been being issued industrial analogue radios manufactured by Chinese language agency BaoFeng, which had been unencrypted and offered much less assorted performance than industrial smartphones. This incentivized using private mobiles throughout the opening months of the warfare, whereas continued sanctions and logistical ineptitude has meant that some Russian forces proceed to speak utilizing such strategies out of necessity.
One of the putting penalties of the Russian army’s OpSec failures in Ukraine is that civilians inside and past Ukraine are aiding the AFU in figuring out Russian troop actions, in some instances even offering concentrating on knowledge utilizing OSINT gathered on-line. All through the battle, the AFU has relied on a unfastened community of partisan supporters working behind enemy traces to help them in buying and verifying vital intelligence, with the Ukrainian intelligence companies having fielded smartphone purposes designed to help civilians in geolocating Russian army gear. The outstanding use of OSINT in opposition to Russian forces has additional strategic impacts past the battlefield, as worldwide observers are exploiting these OpSec failures to gather proof of warfare crimes and counteract Russian political narratives so as to undermine the Russian authorities’s worldwide credibility. It’s price noting that regardless of the numerous materials help the AFU has obtained from its western allies, they too nonetheless depend on conscripted troopers with restricted coaching and stay unable to provide encrypted communications options to all of their forces. This has meant that many AFU items such because the Territorial Protection Forces and the Overseas Legion to depend on private cellphones to speak on the battlefield, whereas many additionally publish fight footage and pictures to social media. Nonetheless, the AFU has made a concerted effort to standardize OpSec practices and instill communications self-discipline by coherent coaching and management. So long as the Russian armed forces fail to duplicate the AFU’s successes, they’ll stay at an virtually deadly strategic drawback for the rest of the battle.